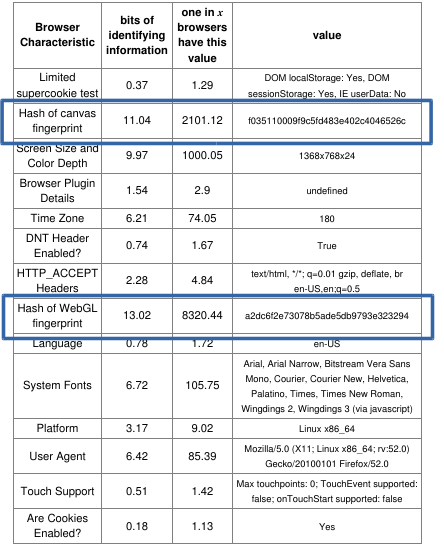
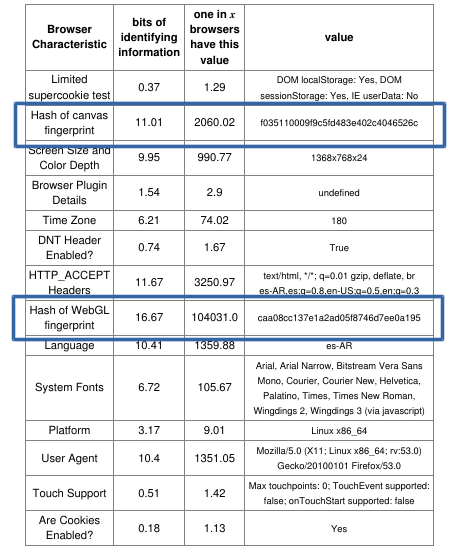
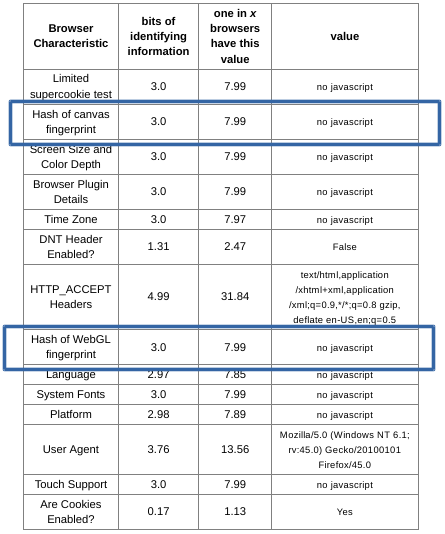
Hi, this time a post about privacy and some recommendations about protecting what is yours and nobody can take away: your privacy. In a world where the technology has evolved in complexity that most do not understand how it works it is important to help people learn that they have civil rights and they should be protected.
One way to store private information is the cloud. This is not the only way and this is probably not the best way, but i guess it is a good way.
We will create a storage to place there what ever you want, it could be passwords, receives, images. We will use two methods to encrypt the data and one to obfuscate it, you can choose the steps, the order, the amount of passwords, that would make it unique and very hard for somebody to get it.
You will use LUKS, gpg and a perl oneliner.
LUKS is a specification of a ciphered disk.
GPG or GnuPG is a complete and free implementation of the OpenPGP standard as defined by RFC4880.
Protecting your data
- Create the LUKS disk.
fallocate -l 1G 4youreyesonly.disk
root@arsat:/home/walter# cryptsetup luksFormat 4youreyesonly.disk
WARNING!
========
This will overwrite data on 4youreyesonly.disk irrevocably.
Are you sure? (Type uppercase yes): YES
Enter passphrase:
Verify passphrase:
root@arsat:/home/walter# cryptsetup luksOpen 4youreyesonly.disk first
Enter passphrase for 4youreyesonly.disk:
root@arsat:/home/walter# mkfs.ext3 /dev/mapper/first
mke2fs 1.42.12 (29-Aug-2014)
Creating filesystem with 261632 4k blocks and 65408 inodes
Filesystem UUID: 6f1c79b7-f1d5-4e05-b821-ead9ad9afdd0
Superblock backups stored on blocks:
32768, 98304, 163840, 229376
Allocating group tables: done
Writing inode tables: done
Creating journal (4096 blocks): done
Writing superblocks and filesystem accounting information: done
2) Store some data inside the disk
mount /dev/mapper/first /mnt/usb/
cd /mnt/usb
root@arsat:/mnt/usb# ls -ltr
total 20
drwx------ 2 root root 16384 Apr 30 00:28 lost+found
-rw-r--r-- 1 root root 47 Apr 30 00:29 notes
root@arsat:/mnt/usb# cat notes
Protect this data:
Cipher, backup, restore.
root@arsat:/mnt/usb#
3) Now close the LUKS disk. Unmount and close it.
cd
umount /mnt/usb
cryptsetup luksClose first
4) In this step you will cipher the disk with gpg. Look that after ciphering it you will have a new file with the “.gpg” extension. Notice that it is smaller, that is because while ciphering it, given the CAST5 algorithm that gpg uses, it probably resumes the zeroes from the file.
gpg -c 4youreyesonly.disk
-rw-r--r-- 1 root root 1073741824 Apr 30 00:29 4youreyesonly.disk
-rw-r--r-- 1 root root 35226974 Apr 30 00:31 4youreyesonly.disk.gpg
5) Now you can flip the file to make it harder to be recognized.
perl -pe 'BEGIN{$/=\1} $_ = pack("C", unpack("C", $_) ^ 0xff)' < 4youreyesonly.disk.gpg > 4youreyesonly.disk.flipped
6) Validate that the files a different.
root@arsat:/home/walter# md5sum 4youreyesonly.disk.gpg
f1c2ae655f52b7f78b477a887847649a 4youreyesonly.disk.gpg
root@arsat:/home/walter# md5sum 4youreyesonly.disk.flipped
d4ce830d575094aa8e88f3409cb46c8d 4youreyesonly.disk.flipped
root@arsat:/home/walter# file 4youreyesonly.disk.gpg
4youreyesonly.disk.gpg: GPG symmetrically encrypted data (CAST5 cipher)
root@arsat:/home/walter# file 4youreyesonly.disk.flipped
4youreyesonly.disk.flipped: data
You can now probably upload the file “4youreyesonly.disk.flipped” to any public place that nobody will know nor the methods used, the order and the passwords.
Recovering your data
Now the time has come to recover the data.
- Un flip the file
perl -pe 'BEGIN{$/=\1} $_ = pack("C", unpack("C", $_) ^ 0xff)' < 4youreyesonly.disk.flipped > 4youreyesonly.disk.original
2) Gpg decipher:
gpg -o 4youreyesonly.original -d 4youreyesonly.disk.original
3) Open it with LUKS:
cryptsetup luksOpen 4youreyesonly.original first
4) Finally open it.
mount /dev/mapper/first /mnt/usb
root@arsat:/home/walter# cat /mnt/usb/notes
Protect this data:
Cipher, backup, restore.
root@arsat:/home/walter# umount /mnt/usb
root@arsat:/home/walter# cryptsetup luksClose first
Ok and that should be all for now. I hope you liked it and please keep spreading with your friends how to protect yourself from intrusion of anybody.